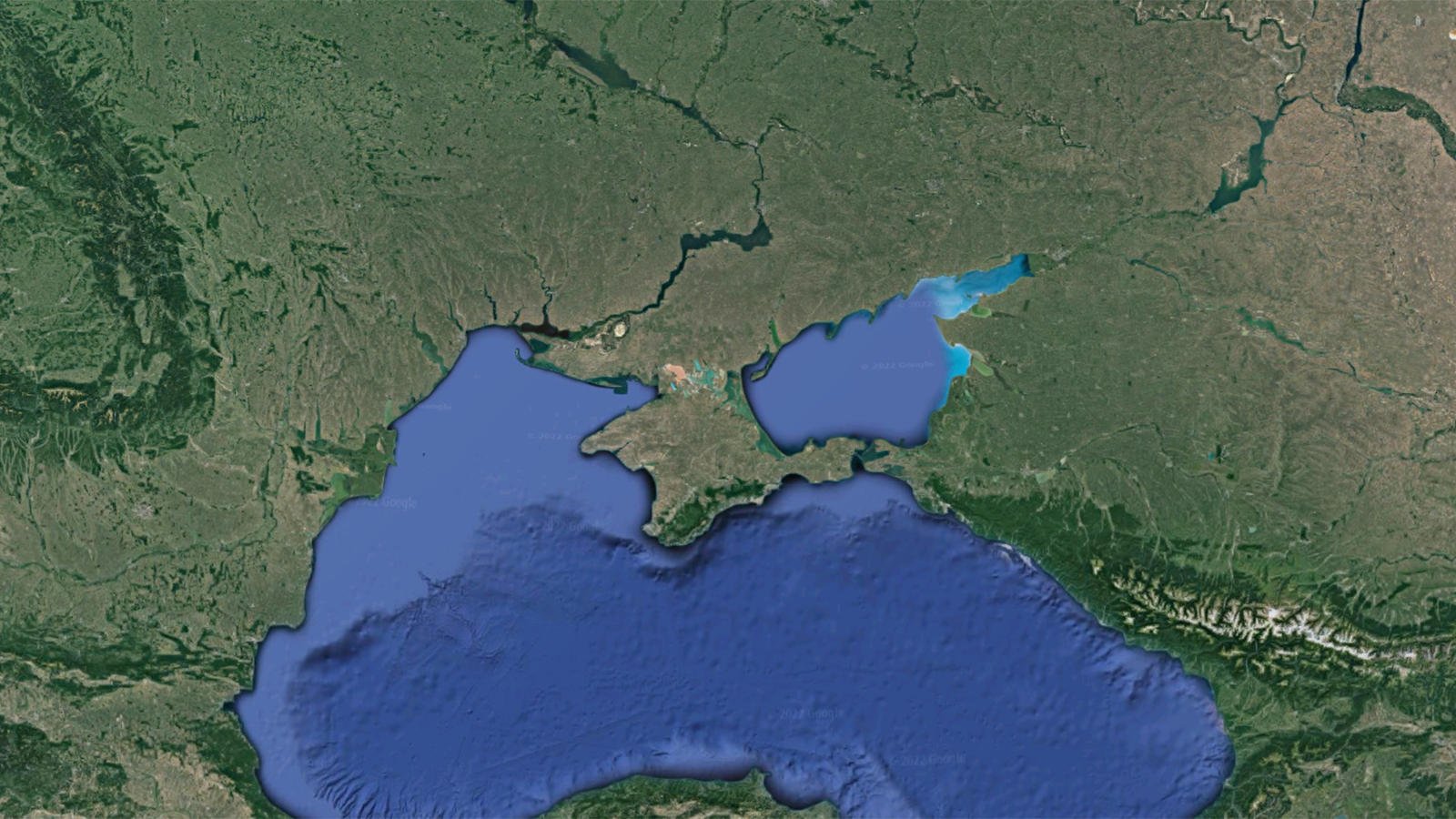
A satellite view of the Black Sea, southern Ukraine and southern Russia. (Google Maps)
WASHINGTON: Localized Russian jamming of GPS signals in Ukraine has been detected by US forces in the region, but so far has not interfered with US support operations, according to Pentagon officials.
One military source told Breaking Defense that jamming has been detected as far out as the Black Sea by US reconnaissance aircraft, but the source stressed it hasn’t had any impact on mission capability.
Similarly, when asked about Russian jamming, a US Space Command spokesperson said, “There are no impacts to U.S. and Allied forces in Europe at this time.”
That said, a senior defense official told reporters today that the US suspects Russia has been holding back in utilizing its vast toolset for electronic warfare so far.
“We have not seen what we believe [are] the full scope of their electronic warfare capabilities brought to bear. Cannot give you an assessment of why that would be. But we do know and we do have indications that in some places they have used EW to their advantage, particular in jamming, at a local level,” the senior official said.
It’s unclear if the jamming has had an effect on Ukrainian operations in-country. That the localized jamming hasn’t been a factor for US operations further away should not come as much of a surprise, former and current Defense Department officials with expertise on the issue said, given the challenge for adversaries to jam the GPS receivers used by US military forces — in particular, military aircraft.
For all of Breaking Defense’s coverage of the Ukraine situation, click here.
“Modern aircraft GPS antennae have the ability to null multiple GPS jamming signals at the same time — that added to the natural jam resistance of a properly keyed and locked GPS receiver make it a near impossibility to jam aircraft unless they are extremely close to a jammer (within multiple kilometers),” one former Pentagon official said.
The Russian military has routinely jammed GPS receivers in eastern Ukraine since the Crimean conflict in 2014, and often spoofs GPS simply to disguise President Vladimir Putin’s movements around Moscow, according to a 2019 report by the nonprofit Center for Advanced Defense Studies.
Indeed, localized jamming of terrestrial GPS receivers — rather than jamming or cyber attacks on the 30 GPS satellites currently operated by the Space Force — has become almost routine, since the 1998 Kosovo war, in many of today’s conflict zones such as Syria, experts say.
For example, the US Maritime Administration “has sort of standing warnings” to ships navigating in the eastern Mediterranean about GPS signal degradation, explained Dana Goward, president of the Resilient Navigation and Timing Foundation.
And while it is extremely hard to jam the encrypted GPS capabilities deployed by the US military, civilian users are not so lucky.
“In terms of the civil versus military GPS … civil GPS is relatively easier to jam and spoof. The Russians have done it on a pretty regular basis across the across the world,” Ganesh Pattabiraman, CEO of NextNav, told Breaking Defense.
NextNav provides terrestrial based receivers to provide alternate positioning, navigation and timing (PNT) signals for use in urban canyons where GPS access is often lost, and Pattabiraman said the firm has been involved in Army experiments seeking alternate PNT solutions.
“Spoofing” the civil GPS signals by altering data so that a device appears in a different location or time zone is even easier for malicious actors, several experts noted, and for that reason is a concern for DoD as well. The Pentagon’s Defense Innovation Unit on Feb. 10 awarded a contract for an unspecified amount to Orbital Insight to detect spoofing of Global Navigation Satellite Systems (GNSS), including GPS.
Secure World Foundation’s 2021 Global Counterspace Capabilities report cites past spoofing incidents in the Black Sea and Syria by Russian forces, by Iran in the Straits of Hormuz and China in the Spratly Islands.
In 2021 the Trump administration issued a new policy, Space Policy Directive 7 (SPD-7), to improve GPS, as well as kick-start investment in alternative PNT systems. In particular, the directive pushed the Defense Department to increasingly focus on making GPS signals more jam resistant, as well as improving cybersecurity.
At the same time, the Transportation Department’s long-awaited Complementary PNT and GPS Backup Technologies Demonstration Report was released, which recommended that the US government as a whole move to invest more in commercial alternatives despite the fact that no one system currently available can provide a stand-alone backup to GPS.
However, experts said there has been little forward movement towards figuring out how to backup GPS for civil and commercial uses in the US. The Biden administration has proposed $17 million in funding for resilient civil PNT in the Transportation Department budget for fiscal year 2022, up from $5 million in 2021.
“Unfortunately, since then Congress did not necessarily take steps to, you know, provide funding to truly make it a nationwide capability,” Pattabiraman said.
Further, there is no one stop shop to even warn commercial operators in the US or abroad about problems with GPS.
“There are government agencies that have responsibilities to warn folks,” Goward said, including the National Geospatial-Intelligence Agency (NGA) and the Department of Homeland Security. “But the challenge is a lot of the sources that they use are classified sources to find out this information. My impression is … one, they haven’t decided it’s important enough to provide these warnings, and two, they haven’t figured out a way to sort of mix open source and classified together and produce the warning.”
An NGA spokesperson was unable to provide comment.
HASC pushes for reciprocity guidance for cloud computing in draft NDAA language
The legislation proposes that if one office in the department officially deems a “cloud-based platform, service, or application” is sufficiently cybersecure to use, then all parts of DoD can accept this ATO.